Axie Infinity’s Ronin Bridge Hack for $551M worth of crypto assets could paradoxically lead to higher rates of blockchain adoption by showing that it’s a lot easier to track stolen cryptocurrency than people think.
The popular misconception that cryptocurrencies are private and untraceable fuels the equally popular misconception that it’s impossible to track and recover stolen crypto assets.
In fact, even some of the most high-profile and sophisticated crypto theft operations have been exposed through the use of blockchain forensics and crypto investigations.
The infiltration of Sky Mavis leading to the Axie Infinity Ronin bridge exploit and the subsequent postmortem is a perfect example.
How Axie Infinity’s Ronin Bridge was Hacked
In short, it was a phishing attack against employees at Sky Mavis that led to a successful 51% attack on the Ronin network, but let’s start at the beginning.
Axie Infinity was at one time the world’s most popular play-to-earn blockchain game. It has its own layer 2 blockchain called Ronin, built on Ethereum. In order for users to transfer funds from the Ethereum blockchain to the Ronin blockchain, a bridge is required. This is what we’re referring to when we talk about the Ronin bridge.
Bridges require sufficient liquidity on both blockchains so they can effectively facilitate transfers for users in a timely manner, and it’s this liquidity in the Ronin bridge that was targeted.
Sky Mavis is the name of the company that developed both the Ronin network and the Axie Infinity game.
Reports have surfaced since the incident which suggest that an employee at Sky Mavis was compromised through a fake job offering that he initially received via the popular networking website, LinkedIn. After several rounds of interviews, the targeted employee was sent a PDF which contained malware that allowed the attackers to infiltrate Sky Mavis’ IT infrastructure and gain access to their internal network.
The Ronin blockchain had 9 validators at the time of the attack, meaning that control of only 5 validators would be sufficient to lead a 51% attack and forge transactions to drain the liquidity from the Ronin bridge. 4 validators were operated by Sky Mavis.
Once the attackers gained control of Sky Mavis’ 4 validators, it left them just 1 validator short of success. They were able to gain control of a 5th validator (operated by the Axie DAO) through a backdoor in Ronin’s gas-free RPC node. With control over 5 of 9 validators, the attackers were then able to forge 2 separate transactions, sending ETH and USDC valued at more than $551M to their own wallet.
Confusion about How Much was Stolen
Many top 10 crypto hacks listicles have the Axie Infinity Ronin Bridge hack at the top of the list with the value being $625M, but it’s not so simple.
According to the Ronin Network’s postmortem report, 173,600 ETH were stolen along with 25.5 million USDC on March 23, 2022, and the price of ETH closed at $3,028 that day. Those figures add up to approximately $551M. However, the price of ETH rose as high as $3,521 by April 3, just 11 days later, which would bring the total value of the hack closer to the widely reported $625M.
Given that the attackers were engaged in various methods of laundering the stolen funds through ETH’s volatility in the days and weeks after the incident, such as using crypto mixers like Tornado Cash and Blender io, decentralized exchanges such as Uniswap, and even centralized exchanges like Binance as cashout points, all with varying degrees of success, it can be debated how much they technically stole.
The graphic below from Chainalysis shows the complicated web of methods used to launder the funds.
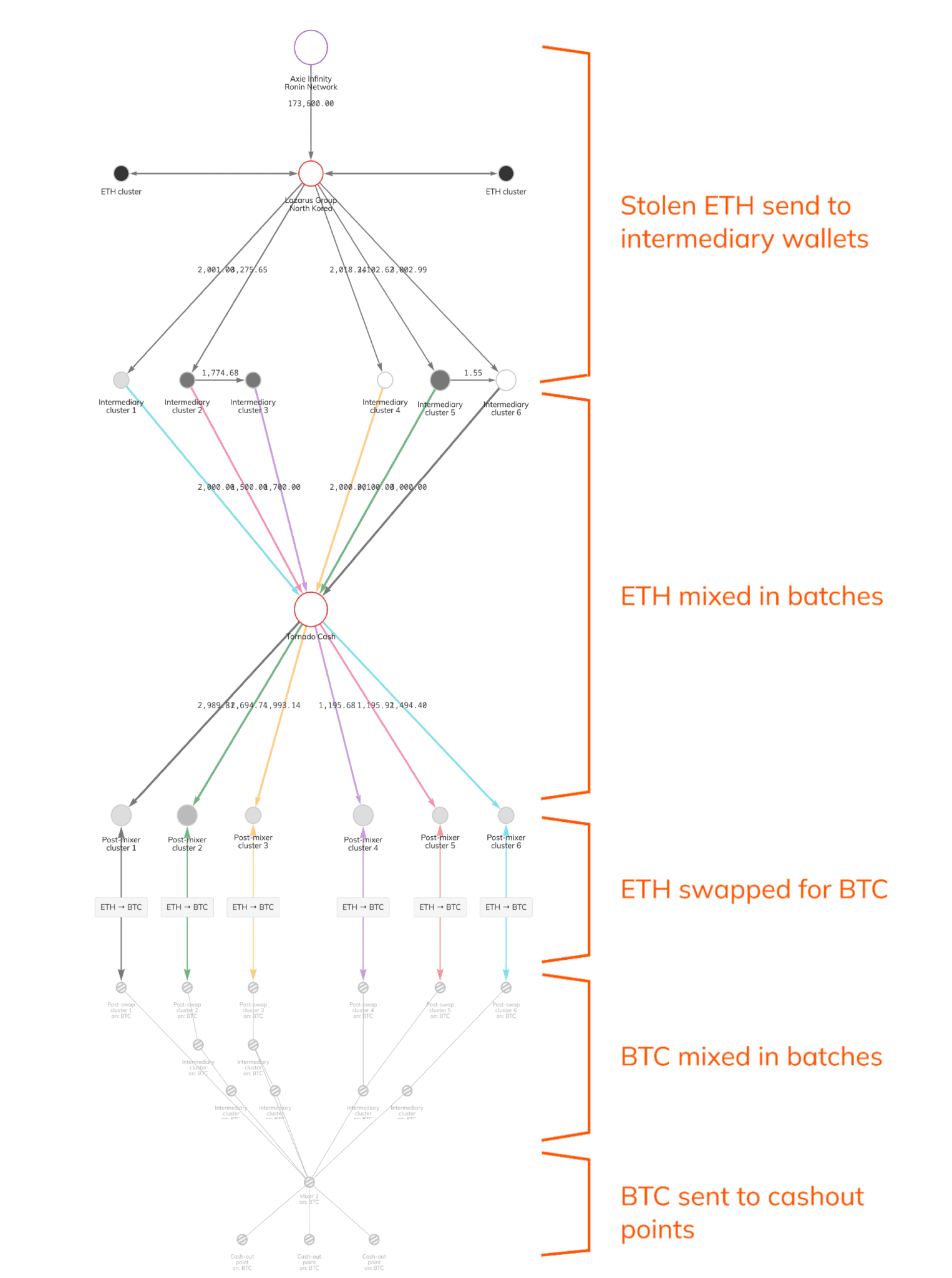
Source: https://blog.chainalysis.com/reports/axie-infinity-ronin-bridge-dprk-hack-seizure/
Regardless, at the time of the attack the assets were worth $551M.
This would put the Ronin Bridge hack at number 4 on the list of biggest crypto hacks, as of October 2022.
Who was Behind the Ronin Bridge Hack?
This is where it gets interesting.
Who would have the resources to run such a sophisticated operation?
A July 2022 report by ESET Research identified the group behind a series of fake job offers in the aerospace and defense sectors similar to the ones received by employees at Sky Mavis. The group was none other than state-sponsored North Korean APT (advanced persistent threat) cybercrime organization Lazarus Group.
The U.S. Treasury Department had already added the Ethereum address associated with the Ronin bridge attack alongside the designation of Lazarus (and its various aliases) to the OFAC SDN list on April 14, 2022, so we now had both pieces of the puzzle confirming who was behind the attack and how it was launched.
Little is known about the Lazarus Group apart from the string of significant cybercrimes that have been attributed to them by researchers between 2010-2021. They fall within the designation of HIDDEN COBRA, a name used by the US Intelligence Community to refer to malicious cyber activity by the North Korean Government in general.
What this Means for the Future of Crypto Adoption
Even the most sophisticated cybercrime operations involving cryptocurrencies sponsored at the state level can be exposed using on and off-chain investigation techniques. Even with the use of advanced laundering strategies and crypto mixers, cybercriminals can be tracked down through the messages they send, the accounts they create, the methods they use and a plethora of other identifiers. This flies in the face of the common perception.
While there are novel threats and new vulnerabilities to be exploited through the use of blockchain technology, DeFi applications, smart contracts, and Web3 in general, there are ways to defend against attackers and ultimately realize a higher degree of security than was available through the centralized nature of so called Web2, and it’s actually easier to recover stolen assets than it is in the real world.
Once a majority of people make this essential recognition, it’s likely that the rate of crypto adoption will persist or even increase.
Marin Ivezic
For over 30 years, Marin Ivezic has been protecting critical infrastructure and financial services against cyber, financial crime and regulatory risks posed by complex and emerging technologies.
He held multiple interim CISO and technology leadership roles in Global 2000 companies.




































































