Tag: FEATURED
IntroductionTrustworthy vs Responsible AITrustworthy AIAttributes of trustworthy AI1. Transparent, interpretable and explainable2. Accountable3. Reliable, resilient, safe and secure4. Fair and non-discriminatory5. Committed to privacy...
The automotive industry has revolutionized manufacturing twice.
The first time was in 1913 when Henry Ford introduced a moving assembly line at his Highland Park...
The rapid development of AI brings both extraordinary potential and unprecedented risks. AI systems are increasingly demonstrating emergent behaviors, and in some cases, are...
Artificial Intelligence (AI) is no longer just a buzzword; it’s an integral part of our daily lives, powering everything from our search for a...
With AI’s breakneck expansion, the distinctions between ‘cybersecurity’ and ‘AI security’ are becoming increasingly pronounced. While both disciplines aim to safeguard digital assets, their focus and the challenges they address diverge in significant ways. Traditional cybersecurity is primarily about defending digital infrastructures from external threats, breaches, and unauthorized access. On the other hand, AI security has to address unique challenges posed by artificial intelligence systems, ensuring not just their robustness but also their ethical and transparent operation as well as unique internal vulnerabilities intrinsic to AI models and algorithms.
Ask most people what they remember from 2016 - if they remember anything at all - and there are usually two big events that...
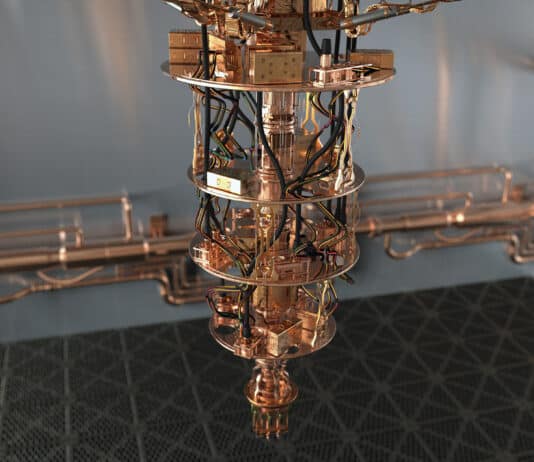
While CRQCs capable of breaking current public key encryption algorithms have not yet materialized, technological advancements are pushing us towards what is ominously dubbed 'Q-Day'—the day a CRQC becomes operational. Many experts believe that Q-Day, or Y2Q as it's sometimes called, is just around the corner, suggesting it could occur by 2030 or even sooner; some speculate it may already exist within secret government laboratories.
Self-help authors and politicians seem to agree on at least one thing: mindset matters. The shelves of bookstores worldwide are awash with motivational books...
The journey towards quantum resistance is not merely about staying ahead of a theoretical threat but about evolving our cybersecurity practices in line with technological advancements. Starting preparations now ensures that organizations are not caught off guard when the landscape shifts. It’s about being informed, vigilant, and proactive—qualities essential to navigating any future technological shifts.
A term first coined by the Japanese government, “Society 5.0” describes "A human-centered society that balances economic advancement with the resolution of social problems...
Neil Harbisson calls himself a cyborg. Without the antenna implanted in his skull, he would not be able to see colour of any kind....
The interest in 5G and mIoT is exploding. It's exciting to see so many IT and cybersecurity professionals in my network trying to learn...
In their outstanding book, Wicked and Wise, Alan Watkins and Ken Wilber look at some of the most pressing ‘wicked problems’ facing the human...
The human will to innovate is seemingly relentless. The history of our species is one of continual development, with the last 350 years, in...
The secret sauce of quantum computing, which even Einstein called "spooky," is the ability to generate and manipulate quantum bits of data or qubits. Certain computational tasks can be executed exponentially faster on a quantum processor using qubits, than on a classical computer with 1s and 0s. A qubit can attain a third state of superimposition of 1s and 0s simultaneously, encode data into quantum mechanical properties by "entangling" pairs of qubits, manipulate that data and perform huge complex calculations very quickly.